Software Supply Chain Security has never been more critical in technology. With an ever-increasing reliance on software applications, ensuring their integrity and safeguarding them from vulnerabilities and malicious actors is paramount. In this Tech Byte, Software Engineer & Cloud Architect for Cura Healthcare, Thomas Vitale, will shed light on the pressing need to enhance software supply chain security as well as offer strategies to address the challenges.
By Thomas Vitale, Software Engineer & Cloud Architect for Cura Healthcare
Defining the Software Supply Chain and Why You Should Care About its Security
First things first: Building software is typically done as an answer to solving a problem. For example, a customer might approach you with a specific problem that you believe can be solved via software. The software supply chain is the set of everything needed to deliver software to production, including code, dependencies, tools, practices, and people. Therefore, securing the supply chain is all about managing risks that might affect any of the activities in the software development lifecycle and ensuring protection against potential vulnerabilities.
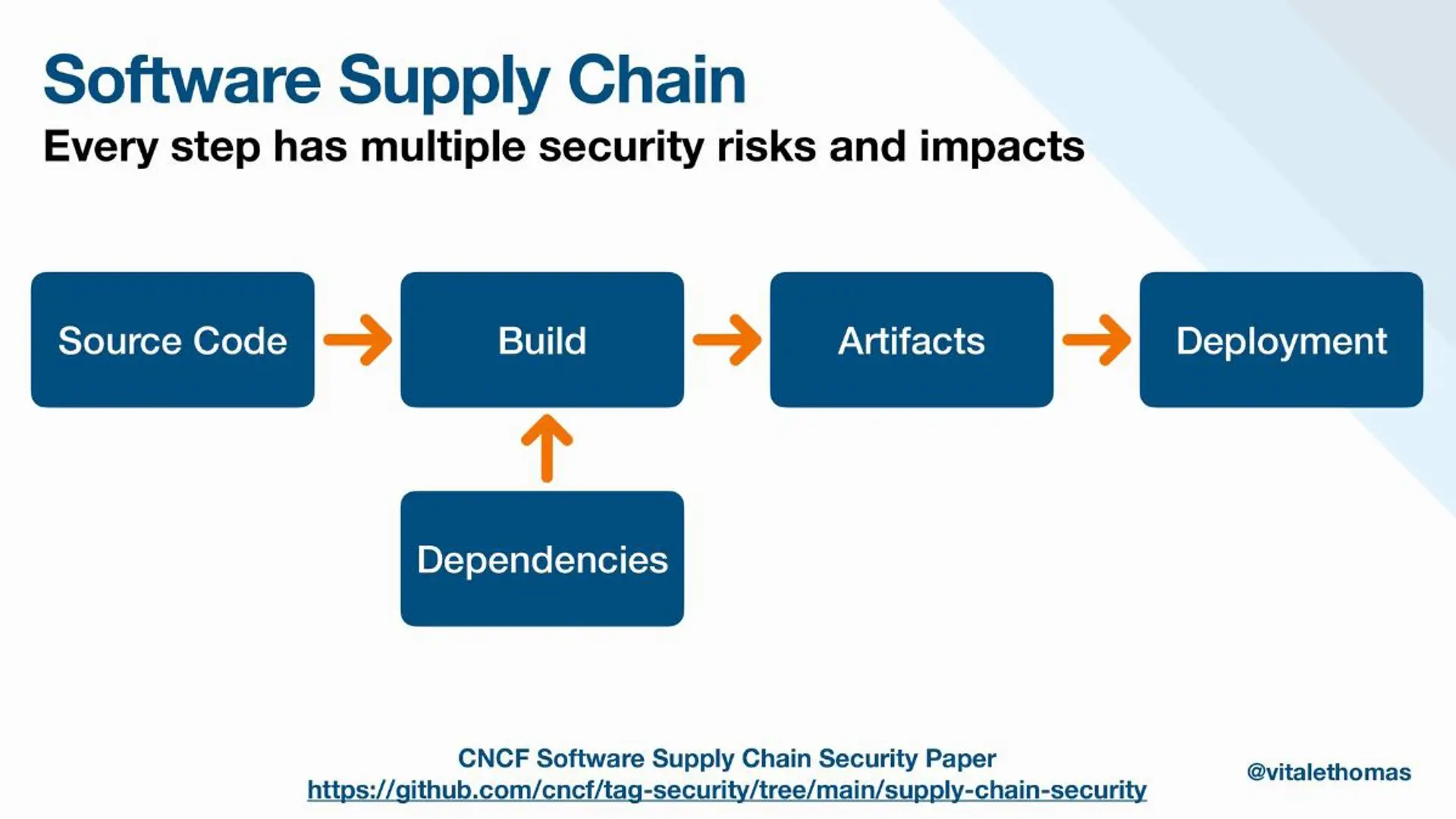
Six Key Concerns And The Strategies to Address Them in Your Java Application
Do you have complete visibility of all the libraries and dependencies in your application JARs and container images? Can you trust the results of your vulnerability scanner? Are your Git commits being manipulated without your knowledge? How can you verify the integrity of your applications in production? How do you ensure effective patching strategies? These are some of the questions of concern that we will explore below.
1. Dependency Management
Secure dependency management is the cornerstone of supply chain. Your Java application relies on numerous external libraries and dependencies to function properly. Ensuring that you have complete visibility into these components is crucial for identifying potential vulnerabilities and addressing them promptly to mitigating vulnerabilities.
To enhance the security of your Java application's supply chain, consider implementing a comprehensive dependency management strategy based on SBOMs. A Software Bill of Materials (SBOM) provides a “list of ingredients” that compose your software. Using a standard like CycloneDX, you can generate an SBOM for your Java application and use it to get detailed insights into your application’s dependencies, associated vulnerabilities, license information, and more.
2. Vulnerability Scanning
Vulnerability scanning is a critical part of maintaining the security of your Java applications' supply chain. It allows you to identify potential weaknesses and security issues within your code and container images. However, to ensure the reliability of your vulnerability scanning results, you need to use trusted tools and techniques.
After generating a high-quality SBOM for your Java application as mentioned in the previous point, you can use the SBOM as input for vulnerability scanning tools and obtain more accurate and actionable insights into potential risks. Regularly scan your applications, apply patches and updates as needed, and establish a process for verifying the effectiveness of your remediation efforts.
3. Git Commit Authenticity
With the distributed nature of modern software development, multiple team members may contribute to a project, making it essential to verify the source of changes: Git commits. Protecting your Git repositories from unauthorised alterations is the first line of defence against potential supply chain attacks.
To enhance the security of your Java application's supply chain, consider implementing strong access controls, code review processes, and digital signatures for commits. By doing so, you can significantly reduce the risk of code tampering and maintain the integrity of your software source code throughout its development lifecycle.
4. Artefact Integrity
Protecting the integrity of your Java applications in production is essential to maintaining a secure supply chain. One effective strategy is to use digital signatures and verification techniques to ensure that the artefacts have not been tampered with.
Digital signatures provide a way to verify the authenticity and integrity of your application's components, including JAR files and container images. As part of the build process, you can sign any application artefact using a tool like Sigstore Cosign and generate verifiable metadata about the build itself to provide provenance information. The SLSA Framework can be used to generate provenance attestations to ensure the integrity of each produced artefact.
This approach adds an additional layer of security to your software supply chain, making it more difficult for malicious actors to compromise your applications during deployment.
5. Patching Strategies
Keeping software up-to-date and secure is ongoing, and therefore maintaining the security of your Java applications must involve effective patching strategies. Regularly applying security patches and updates is essential to address known vulnerabilities and prevent potential exploits. However, this process must be carried out carefully to minimise disruptions to your production environment.
To enhance your supply chain security, consider implementing a well-defined patch management strategy. Prioritise critical security updates and test them in a controlled environment before applying them to your production systems. Automate patch deployment where possible and ensure that you have a rollback plan in case any issues arise.
6. Supply Chain Security for Kubernetes
As more organisations adopt Kubernetes for container orchestration, understanding how to handle supply chain security in a Kubernetes environment is crucial.
To enhance your Java applications' supply chain security, consider implementing Kubernetes-native security practices, such as management solutions like Kyverno that continuously verify signatures, provenance, and vulnerabilities for the containerized applications.
The Developer's Perspective:
In an era where software vulnerabilities and supply chain attacks are becoming more prevalent, the critical importance of software supply chain security is underscored. And as we see from the six most prevalent concerns and strategies addressed here, it's not just a theoretical concern; it has real-world implications for any organisation involved in software development as well as developers and end-users.
In conclusion, enhancing software supply chain security for Java applications is an ongoing and multifaceted endeavour. By addressing the critical concerns and implementing the suggested strategies and techniques, we can bolster the security of our software supply chains and contribute to a safer digital ecosystem for all. My final advice is therefore: Stay vigilant, adapt to emerging security challenges, and prioritise the integrity of your supply chain to ensure the continued success of your Java applications.

